Lead2pass MB6-893 Exam Questions Guarantee MB6-893 Certification Exam 100% Success:
https://www.lead2pass.com/mb6-893.html
QUESTION 21
You are processing a customer payment and want to generate a payment line based on due date so that you can search the invoice lines that meet selected search criteria.
What should you do?
A. Use Settlement
B. Use payment transfer.
C. Use Manual Payment Journal
D. Use Payment proposal

Answer: D
QUESTION 22
Your company decides to use Microsoft Dynamics AX Financials for consolidated financial reporting instead of using Management Reporter.
You need to configure a new legal entity for the consolidated financial transactions.
What must you do to enable the subsidiary company’s transactions to consolidate into the new legal entity that you are creating?
A. Enable the “Use for financial consolidation process” check box in both the consolidated and subsidiary companies.
B. Enable the “Use for financial consolidation process” check box in the subsidiary company.
C. Enable the “Use for financial elimination process” check box in the consolidation company.
D. Enable the “Use for financial consolidation process” check box for the consolidated company.
Answer: D
Explanation:
https://technet.microsoft.com/en-us/library/aa549110.aspx
QUESTION 23
You want a 2% bank charge to appear by default on all electronic methods of payment.
What do you need to set up and then link to the method of payment?
A. terms of payment
B. payment specification
C. payment fee
D. payment control
Answer: C
QUESTION 24
Which form should you use to assign a chart of accounts to a legal entity?
A. Configure account structures
B. General ledger parameters
C. Ledger
D. Legal entities
Answer: C
QUESTION 25
Where do you define the Main account information for bank and cash subledger journal account transactions?
A. On the Bank document posting profiles form
B. On the Bank transaction groups form
C. On the Bank groups form
D. On the Bank accounts form
Answer: B
Explanation:
https://technet.microsoft.com/en-us/library/aa619635.aspx
QUESTION 26
The accounts receivable manager runs a foreign currency revaluation on February 5. The foreign currency revaluation has a considered date of January 31.
The period closing for this revaluation is set for January 31. What is the result of this invoice revaluation if the invoice is settled on February 3?
A. The revaluation includes only documents that have settled amounts on the considered date.
B. The revaluation excludes documents that have been settled on the considered date.
C. The revaluation includes all documents, including unposted, that have open amounts on the considered date.
D. The revaluation includes all documents, excluding unposted, that have open amounts on the considered date.
Answer: D
QUESTION 27
You are setting up taxes on customer invoices.
You need to report a sales tax on the invoice, as and when it is settled, to the tax authorities.
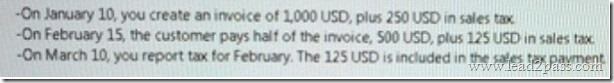
When the customer settles the invoice with the second payment of 625 USD, you report the remaining sales tax.
What should you set up in this situation?
A. Withholding sales tax
B. Sales tax exemption
C. Standard sales tax
D. Conditional sales taxes
Answer: D
QUESTION 28
You are an accounting manager, your company has a new customer, A ledger account must be set up to record the sales tax liability and payments made to the taxing authority in the customer’s specific region automatically.
Which two account groups should you choose for these ledger accounts? Each correct answer presents part of the solution.
A. Settlement account
B. Sales-tax receivable
C. Sales-tax payable
D. Use-txpayable
Answer: AB
QUESTION 29
Your company is using basic budgeting and is planning to configure budget control.
You need to identify the additional configuration that is needed.
Which three components will already be configured as s part of the basic Budgeting setup? Each correct answer presents part of the solution.
A. budget models
B. budget exchange rates
C. over budget permissions
D. budget cycles
E. documents and journals
Answer: ABD
Explanation:
https://technet.microsoft.com/en-us/library/hh242128.aspx
QUESTION 30
You are the accounts receivable manager at you company. The company receives an advance of 10,000 USD against a sales order from the customer.
The tax authorities require the company to re-port the sales tax on the advance amount, even though the sales have not been made.
You need to ensure that this requirement is fulfilled.
What should you do?
A. Report sales tax on prepayment against a prepayment voucher.
B. Report sales tax exemption against a prepayment voucher.
C. Report withholding sales tax against a prepayment voucher.
D. Report conditional sales tax against a prepayment voucher.
Answer: A
MB6-893 dumps full version (PDF&VCE): https://www.lead2pass.com/mb6-893.html
Large amount of free MB6-893 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDdHBxV2xPeXZiSEk